Ignoring Specific Assets
You may spin up cloud servers on the same account that you do not want to be monitored. You can tag these servers with an “ignore tag” of your choosing. Provide a comma-separated list of tags for Ghostwriter to ignore when checking cloud assets. If you use Slack notifications to send reminders to teardown cloud infrastructure, you can also provide a notification delay in days. Ghostwriter will wait to send reminders until a project’s end date + your delay.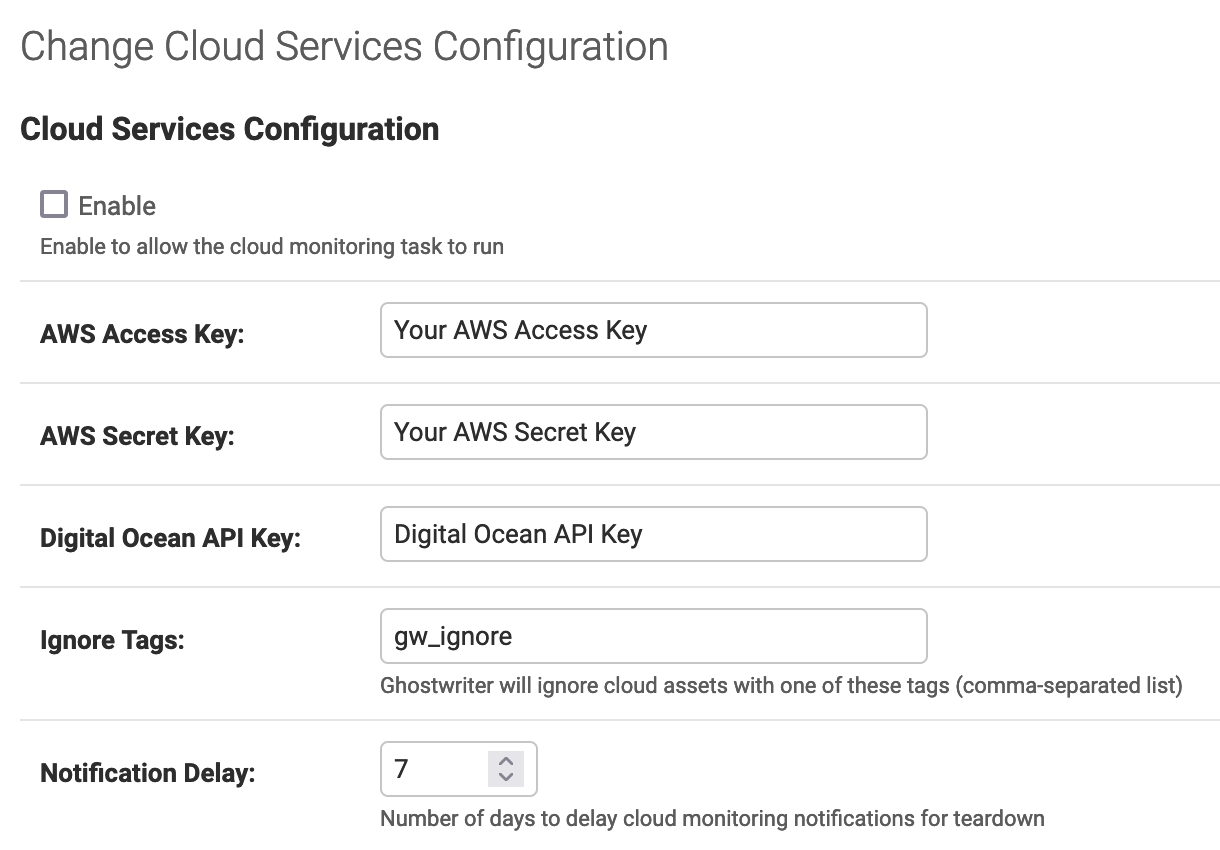
This task is under development to support monitoring Microsoft Azure and additional AWS resources (e.g., Elastic IPs).
Configuring AWS Keys
Ghostwriter is designed to use minimal AWS privileges so you do not need to assign any serious privileges to the keys you use for monitoring your AWS resources. Ghostwriteraccesses and reads from the following services:-
STS – Ghostwriter connects and calls
get-caller-identityto test your keys - Lightsail – Collects your running Lightsail instances and related identifiers
- EC2 – Collects your running EC2 instances and related identifiers
- S3 – Collects your list of buckets
Keep Ghostwriter’s privileges limited. Ghostwriter does not need to be able to upload files to S3 or modify instances, or access storage volumes. The monitoring task only needs to read resource information (i.e., use “Get,” “List,” and “Describe” permissions).
describe-regions and Lightsail’s get-regions.
Then, Ghostwriter uses an EC2 resource to call instances and a Lightsail client to call get-instances to build a list of instances. This data includes:
- ARN
- Name
- State
- Private IP(s)
- Public IP(s)
- LaunchTime
- Tags
- Misc. Networking and Hardware
list-buckets to get a list of all buckets. This data includes the bucket’s name and the date it was created.